Twitter Password Decryptor is the free software to instantly recover forgotten Twitter password from popular 30+ web browsers
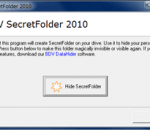
BDV SecretFolder 2010 is a simplest tool for hiding of files and folders on FAT/FAT32 disk. How about creation of secret folder on your USB Flash Drive which you may show or hide with one mouse click? Well, really as easy! For your convenience we have developed BDV SecretFolder 2010 software. You may put it on your Flash Drive — it is portable and takes only 140 Kb.
Oracle Password Recovery and Auditing Software
The protection of your sensitive data is often disregarded. But the encrypting of diaries, pictures or other secret documents with the AES- or Blowfish-Algorithm is relatively simple. With the help of the Easy Encryption Technologie (EEnTe) you need only to enter a password or to insert the EC MoneyCard or certificate smartcard (PKCS). The software in additional support the compressing in the ZIP-format and signing of files.
With over 3 million customers, Disconnect is the easiest way to protect your privacy on all of your devices. Disconnect protects you in 6 ways: Visualize Tracking - see who's following you Encrypted Internet - secure all of your online activity Safe Browsing - block 5000+ trackers Anonymous Search - search privately on Google, Bing, & more Location Control - defeat censorship Privacy Icons - easily decipher privacy policies
AutoKrypt is an encryption software designed for automation that will automatically encrypt or decrypt files and folders. AutoKrypt's encryption methods include password based, public and private key, secret key, OpenPGP password, OpenPGP public and private key.
Digital Signer (Digital Signature) is software that digitally signs PDF documents using X.509 digital certificates. Digital Signer (Digital Signature) is software that digitally signs PDF documents using X.509 digital certificates, pfx file, USB token (digital signature), Hardware token. ideal for bulk signing of a large number of corporate documents rather than signing each one individually.
Bitdefender Internet Security defends you with Product of the Year technology. Extremely fast and non-intrusive, it offers enhanced silent security against e-threats.
Audio Watermarking Tools 2 (AWT2) of www.audiowatermarking.info are software utilities for embedding (and extracting) short data payload within audio streams (wave files). The tools are distributed as a package of GUI and console utilities running on Microsoft Windows, Apple Mac OS X and Linux. The watermark is highly robust. It survives almost all kinds of audio conversions: transcoding using MP3, Ogg Vorbis, air transducing, etc.
The new Panda Free Antivirus provides the easiest-to-use and most intuitive protection for your computer. Install it and forget about viruses, spyware, rootkits, hackers and online fraud. Enjoy real-time protection against the latest malware threats.
Word Password Recovery Lastic introduces a unique approach to cracking Microsoft Word passwords. Unlike other tools, it allows cracking passwords not only in a single document, but in multiple documents at once. The program flawlessly cracks passwords to open and to modify, document protection passwords and VBA passwords. Automatic search discovers password protected documents on your disk that you can crack with a single click.
النسخ الاحتياطي إيبيريوس واحد من الأفضل النسخ الاحتياطي البرمجيات الحرة، كما صدر في طبعات تجارية لأولئك الذين بحاجة إلى النسخ الاحتياطي ميزات متقدمة لشركاتهم. نسخة مجانية من إيبيريوس النسخ الاحتياطي يسمح لك لإجراء نسخ احتياطي لأي جهاز تخزين كبير السعة، مثل محركات أقراص USB الخارجية ومحركات RDX، ناس وأجهزة الكمبيوتر المتصلة بالشبكة. قد جدولة شاملة ومهام إرسال البريد الإلكتروني. وهو يدعم ضغط zip مع أي حد حجم النسخ الاحتياطي التزايدي ومصادقة الشبكة وتنفيذ البرامج والبرامج النصية الخارجية.
كاسبرسكي لمكافحة الفيروسات يحميك من مواقع التصيد والبرامج الضارة التي لن تعرف إلا كانوا يحاولون سرقة منك. في الوقت نفسه، "شبكة الأمن كاسبيرسكي" يسمح جهاز الكمبيوتر الخاص بك إلى التقرير عندما يكتشف تهديد التي لم تشاهد من قبل. يستفيد جميع مستخدمي كاسبرسكي 250 مليون من معرفتنا مجتمعة! وتشمل ميزات كاسبيرسكي: يحمي من الفيروسات وأحصنة طروادة، والديدان، وبرامج التجسس، ادواري مسح الملفات، البريد الإلكتروني والإنترنت المرور "يحمي فورية الرسل يحمي غير معروف التهديدات يحلل" ويغلق "إنترنت إكسبلورر" الضعف تعطيل وصلات لمواقع البرمجيات الخبيثة/مواقع التصيد كتل "الرصد العالمي التهديد" (كاسبيرسكي شبكة الأمن) جميع أنواع keyloggers "التلقائي قاعدة بيانات التحديثات مجاناً دعم المذكرة التقنية": هذا محاكمة تجارية 30 يوما.