Avira AntiVir Rescue System allows users to easily access computers that cannot be booted anymore. Just double-click on the rescue system package to burn it to a CD/DVD. You can then use this CD/DVD to boot your computer.
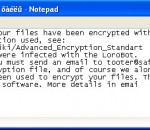
XoristDecryptor is a handy tool that was designed in order to help you fight infections from Trojan-Ransom.Win32.Xorist malware. Malware of the family Trojan-Ransom.Win32.Xorist is designed for unauthorized modification of data on a victim computer. It makes computers uncontrollable or blocks its normal performance. After taking the data as a “hostage†(blocking it), a ransom is demanded from the user.
Free, self-updating software gives your computer full security, protecting your valuable data from any harm. SI Internet Security protects your PC from all types of viruses. Downloading files, music, documents, any files from Internet can be dangerous for your computer. With SI Internet Security you can forget about being cautious. It scans all your downloads and blocks all the malicious programs to secure your computer.
Romaco Timeout is a small and easy to use multi-user time-restriction tool designed to allow a user only so much time on their computer during the course of one day. If they go over this limit, they will be either logged off, or the computer shut down. They will only be able to log back in if the administration password is typed, or until the next day when the quota is reset.
Strong file protection by 128-2048 bit encryption (AES 256-bit and RSA 2048-bit are also supported). Secure file deletion is also supported: U.S. DoD 5200.28, GOST P50739-95 and others. USB Flash Drives can be used as the storage for strong encryption/decryption keys. Creating Self-Decrypting executable files. Powerful command line utility. Ability to encrypt/decrypt files from Windows Explorer in 1-2 mouse clicks.
Today more than ever employers need to be concerned about what their employees are doing on their computers. What seems to be harmless personal use of your company's computers can lead to time consuming and costly legal and security nightmares. The statistics speak for themselves. Don't let your company become one of them. You need to keep a closer eye on what your staff is doing in Cyberspace.
Do you want an antivirus that's powerful, free, and trusted around the world by 230 million users and counting? Then look no further. Avast Antivirus offers powerful Nitro protection designed to protect your PC, without slowing it down.
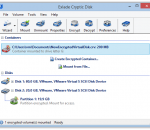
Exlade Cryptic Disk Professional will provide a simple and affordable way to protect disks and disk partitions by encrypting them. The encrypted data cannot be accessed without entering the password, even if a hacker gets access to a PC or the hard drive is stolen.
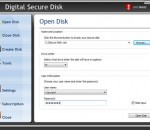
The perfect solution for protecting your sensitive information from theft or other attacks. The program makes a part of your current hard disk into a secure disk. All private and confidential information stored on this disk will be protected by strong encryption. Unlimited disk size, store over 100 GB! In this new version you can also create more than one Secure Disk and move sensitive information in between Secure Disks.
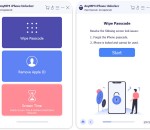
What can I do when forgetting iOS devices lock-screen password, Apple ID or Screen Time passcode? AnyMP4 iPhone Unlocker can hep and get you out by wiping the lock-screen password, Apple ID, Screen Time passcode easily.
النسخ الاحتياطي إيبيريوس واحد من الأفضل النسخ الاحتياطي البرمجيات الحرة، كما صدر في طبعات تجارية لأولئك الذين بحاجة إلى النسخ الاحتياطي ميزات متقدمة لشركاتهم. نسخة مجانية من إيبيريوس النسخ الاحتياطي يسمح لك لإجراء نسخ احتياطي لأي جهاز تخزين كبير السعة، مثل محركات أقراص USB الخارجية ومحركات RDX، ناس وأجهزة الكمبيوتر المتصلة بالشبكة. قد جدولة شاملة ومهام إرسال البريد الإلكتروني. وهو يدعم ضغط zip مع أي حد حجم النسخ الاحتياطي التزايدي ومصادقة الشبكة وتنفيذ البرامج والبرامج النصية الخارجية.
كاسبرسكي لمكافحة الفيروسات يحميك من مواقع التصيد والبرامج الضارة التي لن تعرف إلا كانوا يحاولون سرقة منك. في الوقت نفسه، "شبكة الأمن كاسبيرسكي" يسمح جهاز الكمبيوتر الخاص بك إلى التقرير عندما يكتشف تهديد التي لم تشاهد من قبل. يستفيد جميع مستخدمي كاسبرسكي 250 مليون من معرفتنا مجتمعة! وتشمل ميزات كاسبيرسكي: يحمي من الفيروسات وأحصنة طروادة، والديدان، وبرامج التجسس، ادواري مسح الملفات، البريد الإلكتروني والإنترنت المرور "يحمي فورية الرسل يحمي غير معروف التهديدات يحلل" ويغلق "إنترنت إكسبلورر" الضعف تعطيل وصلات لمواقع البرمجيات الخبيثة/مواقع التصيد كتل "الرصد العالمي التهديد" (كاسبيرسكي شبكة الأمن) جميع أنواع keyloggers "التلقائي قاعدة بيانات التحديثات مجاناً دعم المذكرة التقنية": هذا محاكمة تجارية 30 يوما.