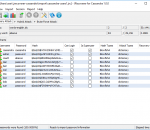
Malicious File Hunter, or MFH for short, is a security software that runs on Windows and allows IT Security Administrators to search for the presence of one or multiple files across their entire network of Windows systems. For example, if a known malicious file is found on one computer, an IT Administrator can use MFH to check if any other system on the network is infected with the same malware. Search query is based on full, partial or wild card
ZoneAlarm protects your PC from phishing attacks, viruses, malware, spyware, and other cyber threats with our advanced security software products. We provide industry-leading security software for both home and small businesses. Our products include powerful antivirus protection, spyware removal, firewall, browser security, ID theft prevention, and more. We support the latest operating systems, including Windows 10, Windows 8 and Windows 7
Audit and recovery of Cassandra passwords. Account information import from databases. Password recovery using dictionary attacks, brute force attacks, hybrid dictionary/brute force attacks. Generation of reports on recovered passwords.
Romaco Timeout is a small and easy to use multi-user time-restriction tool designed to allow a user only so much time on their computer during the course of one day. If they go over this limit, they will be either logged off, or the computer shut down. They will only be able to log back in if the administration password is typed, or until the next day when the quota is reset.
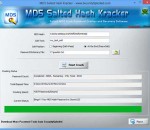
Salted MD5 Hash Password Cracker and Recovery Software
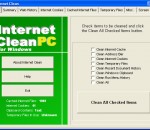
Internet Clean is a handy and reliable utility designed to scan and remove cache files from your Internet browsing history. Internet Clean is able to detect hidden history files and to delete them in a second. It also features a screenshot utility that enables you to watch your kid's computer activity.
RogueKiller x64 offers multilingual support, uses low CPU and RAM, and carries out a scan job rapidly. We have not come across any issues throughout our evaluation, as the app did not hang or crash. Although it is not particularly intuitive or attractive, RogueKiller x64 proves to be a pretty powerful tool for detecting and removing suspicious activity from the system.
In the eventuality that you want to confirm or determine that malware is behind your computer's strange behavior, then perhaps ZHPDiag could lend you a hand. The program does not need an installation per se, but rather you need to agree to the terms and conditions to run it on your computer. Since the operation creates a shortcut on your desktop, the next you can access it from there the next time you need to run it.
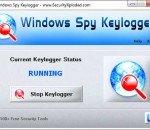
Windows Spy Keylogger is the free software to help you covertly monitor all activities on your computer.
Easy File Protector is a very flexible password protected security utility that restricts access to your files and folders by user-defined time schedule. You choose users, define restricted files/folders and time periods for them, and activate the program. After that, your system disables/enables your files automatically depending on current time and user. Protection is achieved by making files and folders undeletable, unrenamable, unreadable, un
CG Gateway Antivirus allows you to block malware at the gateway before they can enter into your network. The antivirus signature base is updated 48 times per day.
النسخ الاحتياطي إيبيريوس واحد من الأفضل النسخ الاحتياطي البرمجيات الحرة، كما صدر في طبعات تجارية لأولئك الذين بحاجة إلى النسخ الاحتياطي ميزات متقدمة لشركاتهم. نسخة مجانية من إيبيريوس النسخ الاحتياطي يسمح لك لإجراء نسخ احتياطي لأي جهاز تخزين كبير السعة، مثل محركات أقراص USB الخارجية ومحركات RDX، ناس وأجهزة الكمبيوتر المتصلة بالشبكة. قد جدولة شاملة ومهام إرسال البريد الإلكتروني. وهو يدعم ضغط zip مع أي حد حجم النسخ الاحتياطي التزايدي ومصادقة الشبكة وتنفيذ البرامج والبرامج النصية الخارجية.
كاسبرسكي لمكافحة الفيروسات يحميك من مواقع التصيد والبرامج الضارة التي لن تعرف إلا كانوا يحاولون سرقة منك. في الوقت نفسه، "شبكة الأمن كاسبيرسكي" يسمح جهاز الكمبيوتر الخاص بك إلى التقرير عندما يكتشف تهديد التي لم تشاهد من قبل. يستفيد جميع مستخدمي كاسبرسكي 250 مليون من معرفتنا مجتمعة! وتشمل ميزات كاسبيرسكي: يحمي من الفيروسات وأحصنة طروادة، والديدان، وبرامج التجسس، ادواري مسح الملفات، البريد الإلكتروني والإنترنت المرور "يحمي فورية الرسل يحمي غير معروف التهديدات يحلل" ويغلق "إنترنت إكسبلورر" الضعف تعطيل وصلات لمواقع البرمجيات الخبيثة/مواقع التصيد كتل "الرصد العالمي التهديد" (كاسبيرسكي شبكة الأمن) جميع أنواع keyloggers "التلقائي قاعدة بيانات التحديثات مجاناً دعم المذكرة التقنية": هذا محاكمة تجارية 30 يوما.